Ethical Hacking Training in Chennai
Want to obtain your Ethical Hacker certification? Let’s get started. BITA Academy provides the best Ethical Hacking Training in Chennai, instructing you in the most recent hacking tools, methods, and commercial-grade hacking software used by hackers and information security experts to breach a corporation legally. It has created a brand-new framework for learning that employs a four-phase technique: Learn, Certify, Engage, and Compete. After finishing this course, you will be able to use information security controls, legislation, and standards.
What is Ethical Hacking?
A permitted attempt to acquire unauthorized access to a computer system, application, or data constitutes ethical hacking. An ethical hack entails copying the tactics and behaviors of hostile attackers. This procedure aids in locating security flaws that can subsequently be fixed before a malicious attacker can take advantage of them.
Ethical hackers, also called “white hats,” are security professionals who carry out these security evaluations. They contribute to strengthening an organization’s security posture through their proactive activities. The goal of ethical hacking is different from malicious hacking because it is done with permission from the organization or owner of the IT asset.
Roles and Responsibilities of Ethical Hacker
To hack lawfully, ethical hackers must adhere to specific duties and obligations. Ethical hackers will abide by these rules since they know their obligations. Some of the most significant ethical hacking guidelines and responsibilities are listed below:
- Before any security evaluation, an ethical hacker must request the required authorization and consent from the organization.
- They must decide the parameters of their evaluation, make a strategy, and then provide it to the organization with instructions on what to do, when to do it, and how to do it.
- Ethical hackers must report any security flaws and vulnerabilities uncovered in the system or network.
- Keep their findings a secret. Ethical hackers should consent to and abide by their non-disclosure agreement because they aim to secure the system or network.
- After scanning the system for vulnerabilities, these hackers should remove all evidence of their intrusion. By doing this, they stop other malicious hackers from exploiting the system’s vulnerabilities.
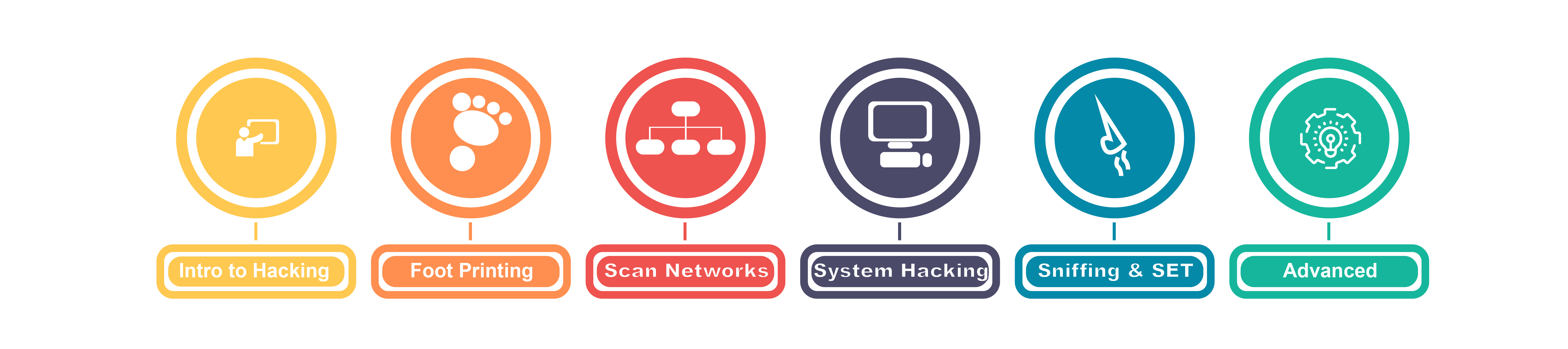
Syllabus for Ethical Hacking Training in Chennai
PART 1: Ethical Hacking – An Overview
- What is Information Security?
- Different Types of Security Attacks
- What do you know about Information Security Threats?
- Do you know about Attack Vectors?
- Deep Dive on Hacking Concepts
- Different Types and Phases of Hacking
PART 2: More About Ethical Hacking
- What do you know about Information Security Controls?
- Physical Security
- How will you perform Incident Management?
- What is Penetration Testing?
- Deep Dive on Information Security Laws
- An Overview of Information Security Standards
PART 3: FootPrinting and Reconnaissance
- Deep Dive on Footprinting Concepts
- What do you know about Footprinting Methodology?
- Different Types of Footprinting Tools
- How to manage Footprinting?
- What do you know about Footprinting Penetration Testing?
PART 4: How to Scan Networks?
- Deep Dive on Network Scanning
- Do you know about CEH Scanning methods?
- PART 5: System Hacking
- How to evaluate info for System Hacking?
- Goals of System Hacking
- Deep Dive on CEH Hacking Methodology (CHM)
- Different Steps to perform CEH System Hacking
- What do you know about Hiding Files?
- Deep Dive on Covering Tracks
- What is Penetration Testing?
PART 6: Deep Dive on Sniffing
- An Overview of Sniffing Concepts
- Different Types of Sniffing
- What do you know about MAC and DHCP attacks?
- Deep Dive on ARP Poisoning and Spoofing Attack?
- What is DNS Poisoning?
- Sniffing Tools
- Deep Dive on Wireshark
- An Overview of Packet Sniffing Tool
- What do you know about Capsa Network Analyser?
PART 7: What do you know about Social Engineering?
- Deep Dive on Social Engineering
- Different methods of Social Engineering
- What is Impersonation on Social Networking Sites?
- Deep Dive on Identity Theft
PART 8: Denial of Service (DoS)
- What is DoS?
- Deep Dive on DoS
- Different methods of attack in DoS and DDoS
- What do you know about Botnets?
- DDoS Case Study with real time examples
- Different Types of DoS and DDoS Attack Tools
- Deep Dive on Protection Tools
- Penetration Testing for DoS and DDoS Attack
PART 9: What do you know about Session Hijacking?
- An Overview of Session Hijacking
- Deep Dive on App and Network Level Session Hijacking
- Different Types of Session Hijacking Tools
- Do you know about Safety Measures?
- How to Perform Penetration Testing?
PART 10: How to Hack WebServers?
- Deep Dive on Web Server
- What do you know about Web Server Attacks?
- Do you know about Web Server Hacking Methodology?
- Different Types of Tools for Web Server Hacking
- What’s the Safety Measures to be followed?
- What do you know about Security Tool?
- Deep Dive on Penetration Testing
PART 11: SQL Injection
- Deep Dive on SQL Injection
- Different Types of SQL Injection
- What do you know about SQL Injection Methodology?
- Different Types of SQL Injection Tools
- Do you know about Evasion methods?
- What’s the Safety Measures to be followed?
PART 12: How to Hack Wireless Networks?
- What is Wireless Network?
- Deep Dive on Wireless Encryption
- Wireless Threats
- Deep Dive on Wireless Hacking Methodology
- Different Types of Wireless Hacking Tools
- What do you know about Bluetooth Hacking?
- Safety Measures
- Deep Dive on Wi-fi Penetration Testing
- Different Types of Wireless Security Tools
PART 13: How to Hack Mobile Platforms?
- Deep Dive on Mobile Platform Attack Vectors
- How to Hack Android OS?
- Do you know to hack iOS?
- How to hack windows phone and blackberry?
- Deep Dive on Mobile Device Management (NIDM)
- What do you know about Mobile Security Guidelines?
- Different Types of Mobile Security Tools
- More about Penetration Testing
PART 14: How to hack Web Apps?
- Deep Dive on Web Application
- What do you know Web App Threats?
- Do you know about Web App Hacking Methodology?
- Different Types of Tools for Web App Hacking
- What do you know about Safety Measures?
- Deep Dive on Security Tool
- How to perform Penetration Testing?
- What do you know Web App Perpetration Testing Framework?
PART 15: How to Evade IDS, Firewalls and HoneyPots?
- Deep Dive on IDS, Firewalls and HoneyPots
- How to Evade IDS and Firewalls?
- Different Types of Tools to Evade IDS and Firewalls
- How to detect HoneyPots?
- Safety Measures
- How to perform Penetration Testing?
PART 16: Cloud Computing
- Deep Dive on Cloud Computing
- What do you know about cloud computing threats and attacks?
- Deep Dive on Cloud Security Tools
- Safety Measures
PART 17: Deep Dive on Cryptography
- Case Study about Heartbleed
- Case Study about Poodlebleed
- Deep Dive on Cryptography
- What do you know about Encryption Algorithms?
- Different Types of Cryptography Tools
- Deep Dive on Public Key Infrastructure (PRI)
- What do you know about Email Encryption?
- Deep Dive on Disk Encryption
- An Overview of Cryptography Attacks
- Deep Dive on Cryptanalysis Tools
Certified Ethical Hacking by EC Council
Part 1: Introduction to Ethical Hacking
- Understanding Information Security
- Terminologies and Elements of Securing Information
- Balancing Security, Functionality, and Usability
- Exploring Threats to Information Security
- Types of Information Security Threats and System Attacks
- Hacking Fundamentals
- What is Ethical Hacking and Its Need
- Types of Hackers
- Breakdown of Hacking Phases
- Skills of Ethical Hackers
- Information Security Controls
- Enterprise Information Security Architecture (EISA)
- Network Security Zones
- Risk Assessment and Management
- Information Security Controls
- Enterprise Information Security Architecture
- Network Security Zones
- Implementing Network Security Controls
- Threat Modeling
- Incident Response and Management
- Handling Incidents
- Security Incident and Event Management (SIEM)
- User Behavior Analytics (UBA)
- Data Backup and Recovery
- Security Testing and Compliance
- Penetration Testing
- Concepts and Significance
- Phases and Methodology
- Blue Teaming and Red Teaming
- Compliance and Legal Framework
- Laws and Standards
- PCI-DSS, HIPAA, SOX, FISMA, DMCA
- Advanced Cybersecurity Topics
- AI and ML in Cybersecurity
- Network Security Controls
- Data Protection Strategies
Part 2: Footprinting and Reconnaissance
- Understanding Footprinting
- Footprinting using Whois
- Several Types of Footprinting
- Website Footprinting
- Email Footprinting
- DNS Footprinting
- Network Footprinting
- Tools for Footprinting (Maltego, Recon-ng, FOCA, Recon-Dog)
- Google Hacking Techniques
- Footprinting Countermeasures
- Footprinting using Penetration Testing
Part 3: Network Scanning
- Concepts of Network Scanning (TCP/IP)
- Tools and Techniques for Scanning (Nmap, Hping2)
- Banner Grabbing
- Network Diagrams and Mapping Tools
- Scanning using Penetration Testing
Part 4: Basics of Enumeration
- Understanding Enumeration Concepts and Methods
- NTP Enumeration
- NetBIOS Enumeration
- LDAP Enumeration
- SMTP and DNS Enumeration
- SNMP Enumeration
- Enumeration Strategies and Techniques
- Enumeration using Penetration Testing
Part 5: Vulnerability Analysis
- Understanding Vulnerability Assessment
- Vulnerability Research
- Types of Vulnerability Assessment
- Vulnerability Scoring Systems (CVSS, CVE, NVD)
- Vulnerability Assessment Tools
- Vulnerability Scanning Solutions
- Evaluating Vulnerability Assessment Approaches
- Functionality of Vulnerability Scanning Solutions
- Crafting and Analysing Vulnerability Assessment Reports
Part 6: Basics of System Hacking
- Exploring System-Hacking Concepts
- CEH Hacking Methodology (CHM)
- Objectives of System Hacking
- Password Cracking
- Types of Password Attack Techniques
- Password Retrieval Utilities
- NTLM Authentication Process
- Kerberos Authentication Process
- Password Salting Mechanism
- Protecting Against LLMNR/NBT-NS Poisoning
- Privilege Escalation Types and Strategies (DLL, Vulnerability, Dylib Hijacking)
- Executing Defence Applications
- File Concealment (Rootkuts, NTFS Data Stream)
- Covering Tracks
- Auditpol for Disabling Auditing
- Log Clearance Methods
- Manual Event Log Purging
- Concealing BASH Shell Tracks
- Camouflaging Network Activity
- Obscuring Operating System Traces
Part 7: Malware Threats
- Understanding Malware Concepts
- Distribution Techniques Employed by Attackers
- Elements of Malicious Software
- Trojan Concepts (Trojan Wrappers, Crypters)
- Virus and Worm Concepts
- Phases in a Virus Lifecycle
- Virus Functionality
- Indicators of Virus Presence
- Malware Analysis
- ZeuS/Zbot Trojan Analysis
- Analyzing WannaCry Virus
Part 8: Sniffing Fundamentals
- Understanding Sniffing Concepts (OSI, SPAN)
- Tools and Techniques for Sniffing (DHCP)
- Understanding Honeypots, Firewalls, IDS
Part 9: Social Engineering
- Social Engineering Techniques (Human-centric, computer-centric, and mobile-centric)
- Insider Threats
- Detecting Phishing Emails
Part 10: DoS and DDoS Attacks
- Understanding DoS/DDoS Attacks and Botnets
- Methods Used in DoS/DDoS Offensives
- The UDP Flood Attack
- ICMP Flood Attack Mechanism
- Ping of Death and Smurf Attacks
- SYN Flood Attack Strategy
- The Fragmentation Attack
- Denial-of-Service (DRDoS)
- Tools and Protective Measures
- DoS/DDoS Penetration Testing for DDoS Attacks
Part 11: Session Hijacking
- Understanding Session Hijacking
- Session Hijacking at the Application Level
- Categories of Session Hijacking
- Session ID Compromise through Client-Side Attacks
- Cross-Site Scripting (XSS)
- Cross-Site Request Forgery (CSRF)
- Session Hijacking at the Network Level
- IP Spoofing and Source-Routed Packets
- RST Hijacking
- Blind Session Hijacking
- Session Hijacking in TCP/IP, UDP
- Tools and Protective Measures for Session Hijacking
Part 12: Hacking Web Servers and Understanding Web Application Hacking
- Understanding Web Server Operations and Web Applications
- Architecture (Open Source Web Servers, IIS Web Servers)
- Causes and Consequences of Web Server Compromises
- Web Server Vulnerabilities and Attacks (MiTM, Phishing, SSH Brute)
- Tools for Web Server Offensives and Web Application Hacking
Part 13: Fundamentals of SQL Injection
- Understanding SQL Injection
- Insights into HTTP POST Requests
- Comprehending Regular SQL Queries
- Grasping the Structure of an SQL Injection Query
- SQL Injection Strategy and Utilities
- Techniques and Preventive Measures to Evade Detection
Part 14: Wireless Network Exploitation
- Wireless Fundamentals
- Wireless Terminologies
- Types of Wireless Networks
- Wireless Encryption
- WEP, WPA, and WPA2 Differences
- The Pitfalls of WEP Encryption
- Tools for Wireless Intrusion
Part 15: Mobile Platform Exploitation
- Mobile Platform Vulnerabilities and Security Tools
- Anatomy of Mobile Assaults
- Mobile Attack Vectors and Platform Vulnerabilities
- Challenges with App Sandboxing
- Android OS and iOS Exploitation
- Android Rooting Techniques
- Network Access Control via NetCut
- Mobile Hacking with zANTI
- iOS Trojans, Apple’s iOS
- Mobile Espionage Software and Device Management
Part 16: IoT Exploitation Fundamentals
- Understanding IoT
- IoT Vulnerabilities and Threats
- OWASP’s Top 10 IoT Vulnerabilities
- Scoping Out IoT’s Attack Surface
- IoT Attacks Across Diverse Sectors
- IoT Hacking Methodology and Mitigation Strategies
Part 17: Basics of Cloud Computing and Cryptography Essentials
- Cloud Deployment Concepts and Models
- Cloud Computing Threats and Attacks
- Domain Name System (DNS) Attacks
- Side-Channel Attacks or Cross-guest VM Breaches
- SQL Injection Attacks
- Cryptanalysis Attacks
- Wrapping Attack
- Understanding Cryptography
- Encryption Techniques and Cryptography Utilities (DES, AES, RSA, PKI)
Ethical Hacking Certification Training
Professionals that handle IT security across infrastructure that spans physical, cloud, and hybrid environments are the perfect candidates for the CEH Certification course. You should pursue the CEH certification once you better understand the ethical hacker’s function. The moral hacking Training in Chennai will assist you in learning about and comprehending network and cyber risks. The Certified Ethical Hacker (CEH) credential can be obtained by understanding computer security. Your cybersecurity knowledge and competence, as well as any cybersecurity-related specialties, are validated by the EC- Council certification exam. You may pass the 312-50 test by taking the Certified Ethical Hacker v12 training course in BITA.
- Certified Ethical Hacker (CEH)
- CompTIA Security+
Job Opportunities in Ethical Hacking
A rise in computer hacking incidents has compelled well-known businesses, financial institutions, and governmental agencies to hire ethical hackers. Ethical hackers assist these businesses in identifying the weaknesses and potential security holes in their computer systems and defend them against any incoming threats. Therefore, a profession in ethical hacking offers bright possibilities for the foreseeable future. The top companies in the IT industry, such as Wipro, Dell, Reliance, Google, Accenture, IBM, and Infosys, are all hiring talented, ethical hackers. A new ethical hacker can currently anticipate earning Rs. 4.8 lakh annually. Candidates with more experience and advanced certifications can earn up to Rs 30 lakh annually. Sign up for Ethical Hacking Training in Chennai.
The following are some of the job positions in Ethical Hacking
- Ethical Hacking Developer
- Ethical Hacker
- Ethical Hacking Trainer
- Penetration Tester
- Information Security Engineer
Why should you select us?
- After completing the Ethical Hacking Training in Chennai, you will be proficient in the most recent hacking tool and its methods.
- We offer the Best Ethical Hacking Training in Chennai Chennai for Professionals and students who want to start their careers in Information Security.
- Our trainer’s teaching skill is excellent, and they are very polite when clearing doubts.
- We conduct mock tests that will be useful for your Ethical Hacking Interview Preparation.
- Even after completing your Ethical Hacking Training in Chennai, you will get lifetime support from us.
- We know the IT market, and our Ethical Hacking content aligns with the latest trend.
- We provide classroom training with all essential preventative precautions.
- We provide Ethical Hacking Online training on live meetings with recordings.